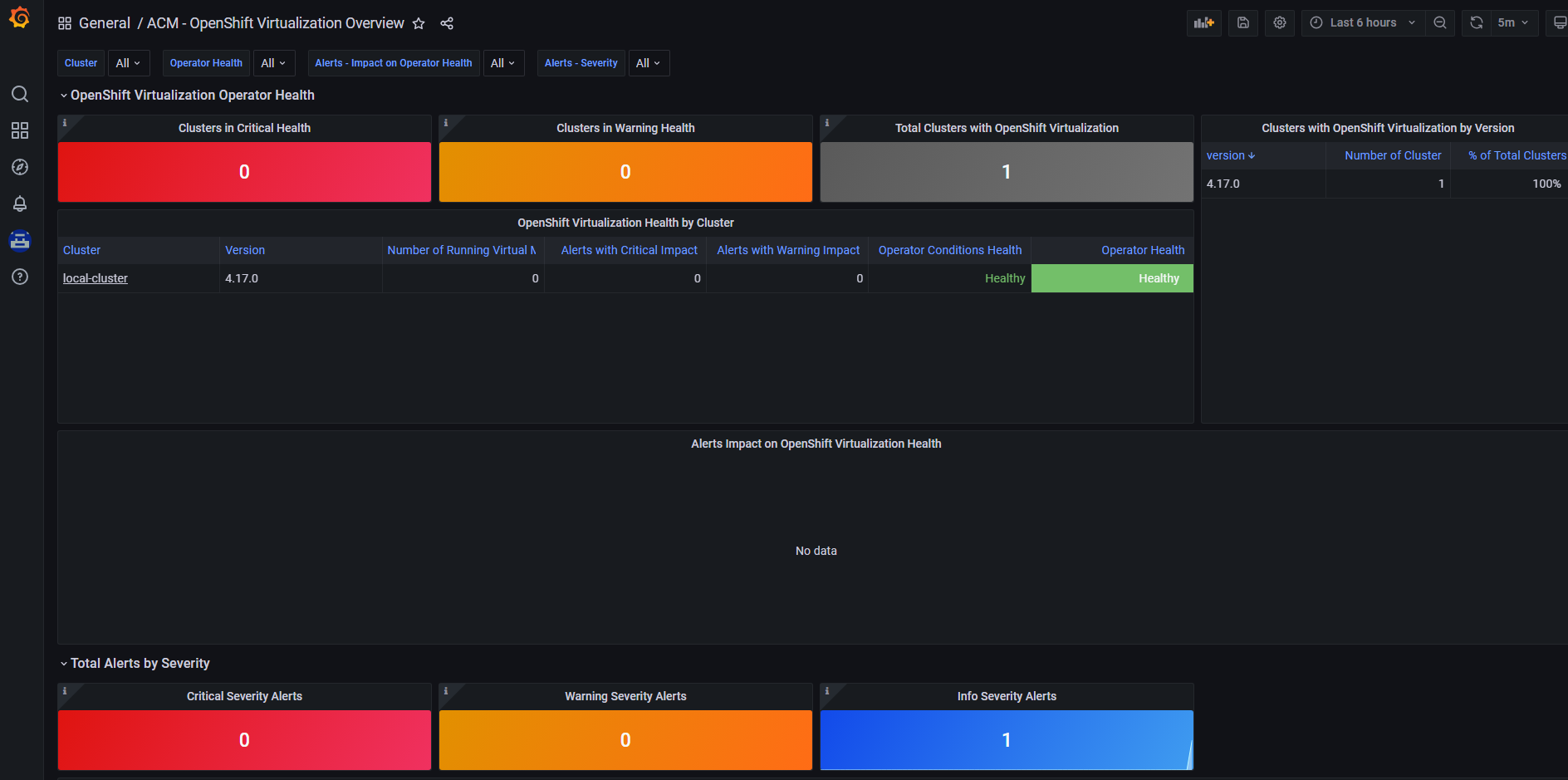
Openshift Virtualization Dashboard in ACM
As of Openshift 4.17, the Openshift Virtualization dashboard is available in Advanced Cluster Management (version 2.11).
To enable this functionality, simply turn on the Observability service. See the following link:
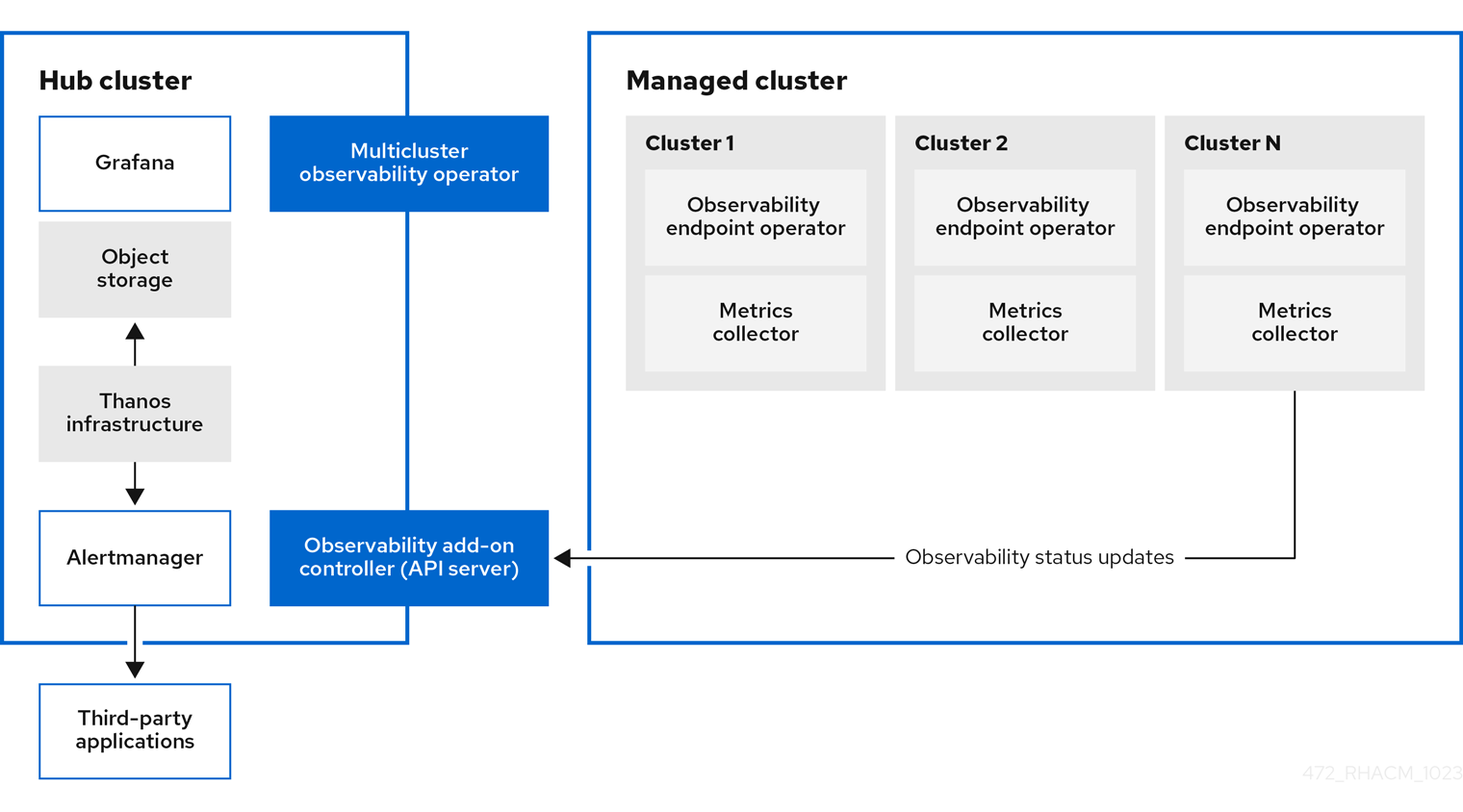
In my cluster I am using Openshift Data Foundation so the S3 storage supplied by Noobaa will be used. The instructions being followed are located at the following link:

Enabling Observability Service
- Create the namespace/project called open-cluster-management-observability.
oc create namespace open-cluster-management-observability- By default, the pull secret was not definied in open-cluster-management namespace, so I copied the global one.
export DOCKER_CONFIG_JSON=`oc extract secret/pull-secret -n openshift-config --to=-`oc create secret generic multiclusterhub-operator-pull-secret \
-n open-cluster-management-observability \
--from-literal=.dockerconfigjson="$DOCKER_CONFIG_JSON" \
--type=kubernetes.io/dockerconfigjson- Let's create the S3 storage that will be used for this using the Openshift Web Console.
Go to Storage --> Object Bucket Claim - Inside the open-cluster-management-observability project, create the claim
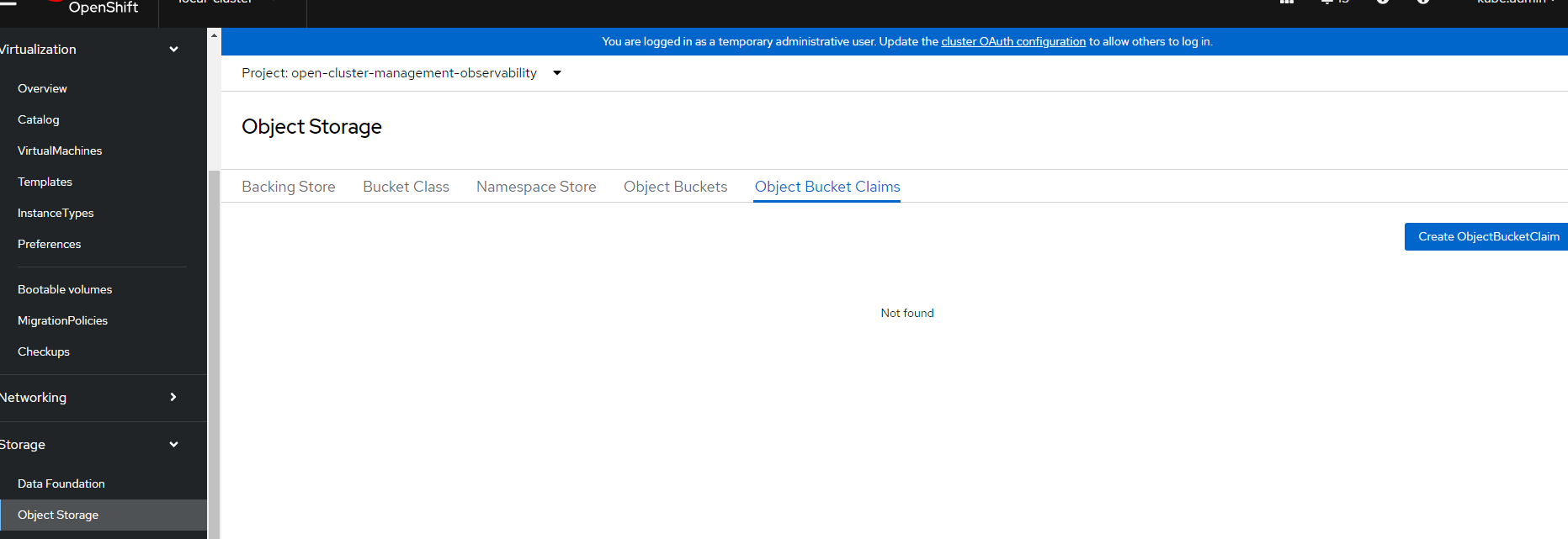
Name: can leave blank to be auto-generated
StorageClass: openshift-storage.noobaa.io
BucketClass: noobaa-default-bucket-class
Click "Create"
- After this object is created go back to Storage --> Object Storage --> Object Bucket Claims
Click on the bucketclaim-<randomuid> OBC (object bucket claim) object.
At the bottom of the resulting screen will the Object Bucket Claim Data
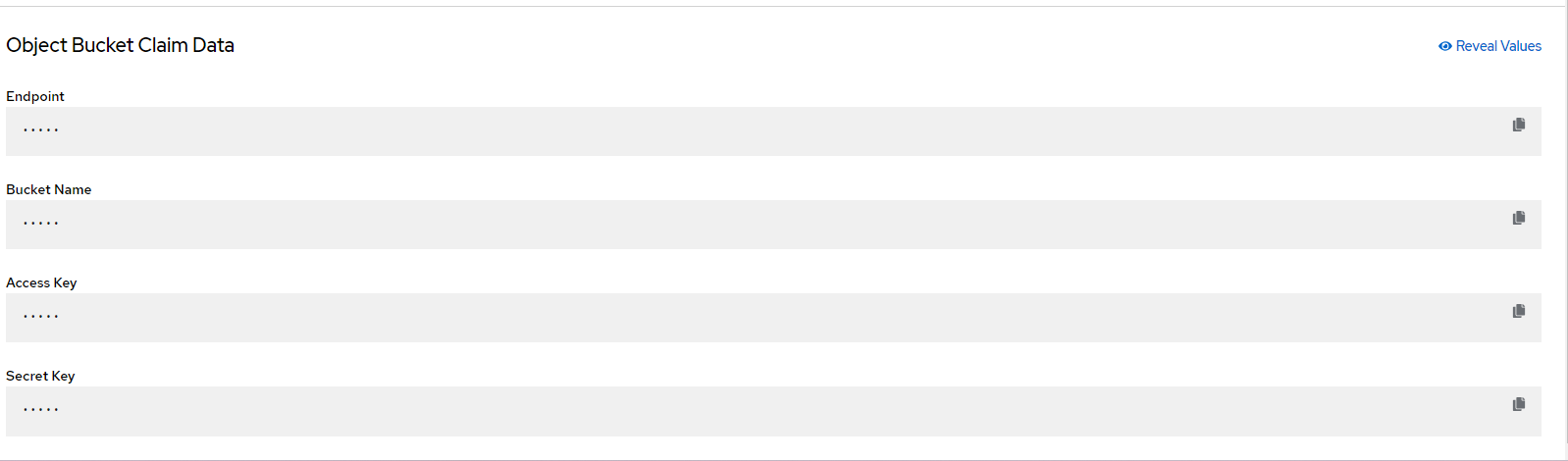
You will reveal each of these properties and use that to fill-in the secret information based on the template below:
apiVersion: v1
kind: Secret
metadata:
name: thanos-object-storage
namespace: open-cluster-management-observability
type: Opaque
stringData:
thanos.yaml: |
type: s3
config:
bucket: bucket--<randomuid>
endpoint: s3-openshift-storage.apps.<clustername>.<basedomain>:443
insecure: false
access_key: <from above>
secret_key: <from above>
http_config:
tls_config:
ca_file: /etc/minio/certs/ca.crt
Once you fill in these values, assuming the file is called secret.yaml
oc apply -f secret.yaml- In order for Thanos to connect to the S3 object store that is part of ODF, the CA will need to be added to the connection.
oc -n openshift-ingress get secret router-certs-default -o jsonpath="{.data.tls\.crt}" | base64 -d > ca.crtoc create secret generic s3-odf-ca --from-file=ca.crt=ca.crt -n open-cluster-management-observabilityapiVersion: observability.open-cluster-management.io/v1beta2
kind: MultiClusterObservability
metadata:
name: observability
spec:
observabilityAddonSpec: {}
storageConfig:
metricObjectStorage:
name: thanos-object-storage
key: thanos.yaml
Assuming this file is called multiobservability.yaml, apply it:
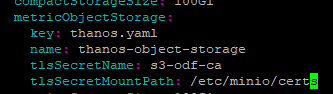
oc apply -f multiclusterobservability.yamloc edit mco observabilityand add the tlsSecretName and tlsSecretMountPath as shown below.
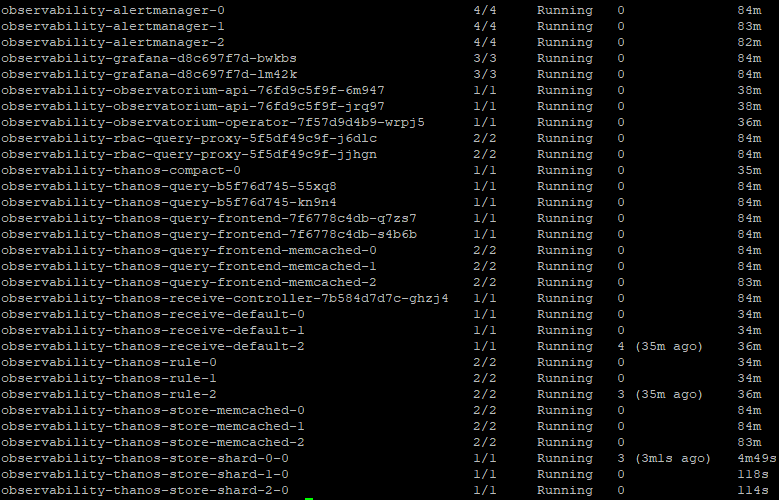
- Shortly, you will see a bunch of pods start in the open-cluster-management-observability namespace/project
- Now go back to the Openshift Web Console and switch to the "All Clusters" perspective/view. The ACM (Advanced Cluster Management) console has been integrated into the main console for some time now.
8. Go to Infrastructure --> Clusters
9. On the right side of this screen, a Grafana option will appear now
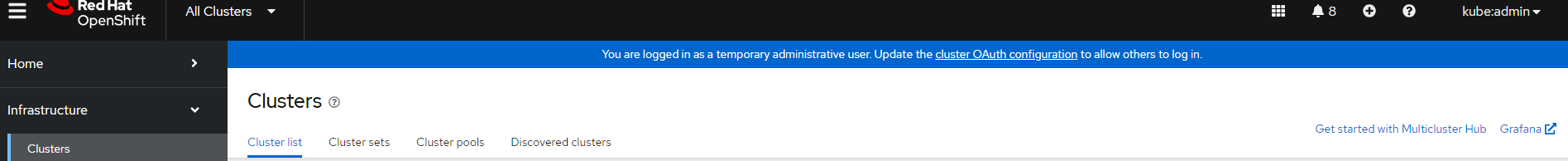
Click on this.
- You may need to temporarily accept certificates and log back in as kubeadmin user for now.
Once you do this, the Grafana page will load. - Click on Dashboards --> Browse
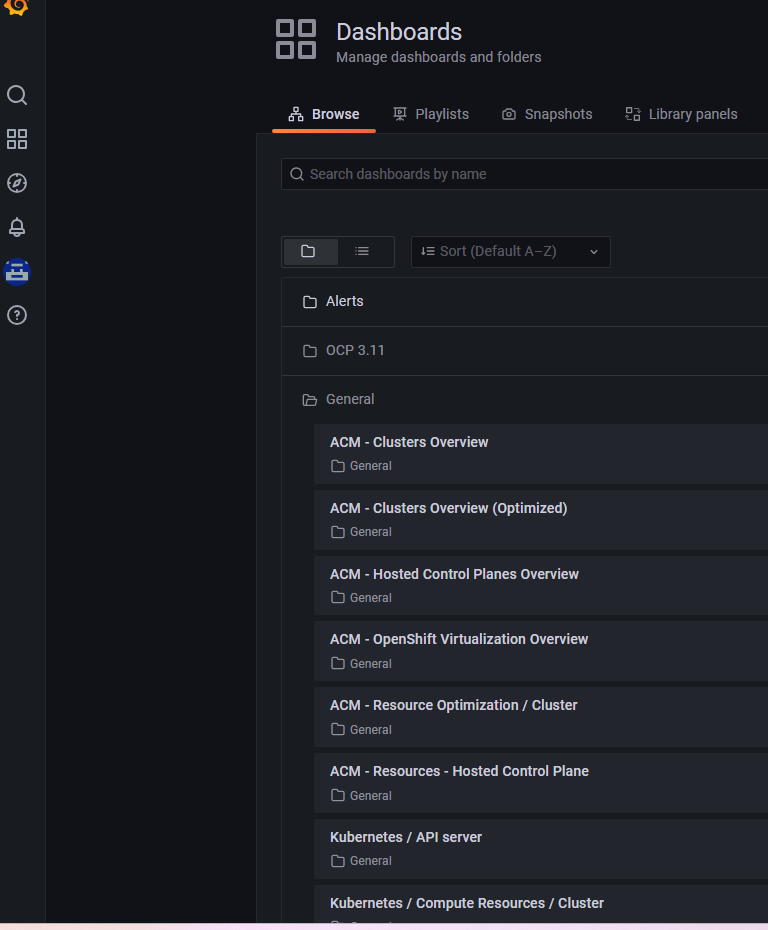
Scroll down to the the General/ACM - Openshift Virtualization Overview dashboard.
Now, you can view some high-level metric data associated with Openshift Virtualization across your fleet of clusters.